Is Remote Monitoring Safe? Data Security in Healthcare Devices
Remote Patient Monitoring (RPM) has revolutionized healthcare by enabling continuous patient care beyond traditional clinical settings. However, as RPM becomes more prevalent, ensuring the security and privacy of patient data is paramount. This article delves into the intricacies of HIPAA compliance, data storage and sharing mechanisms, cybersecurity risks, and best practices to safeguard sensitive health information in 2025.
Understanding HIPAA Compliance in Remote Patient Monitoring
The Health Insurance Portability and Accountability Act (HIPAA) sets the standard for protecting sensitive patient data in the United States. For RPM systems, compliance with HIPAA is not just a legal obligation but a critical component of patient trust and safety.
Key HIPAA Requirements for RPM:
Data Encryption: All electronic Protected Health Information (ePHI) must be encrypted during transmission and storage to prevent unauthorized access.
Access Controls: Implementing strict access controls ensures that only authorized personnel can access patient data.
Audit Trails: Maintaining logs of data access and modifications helps in monitoring and responding to potential breaches.
Business Associate Agreements (BAAs): Healthcare providers must have BAAs with third-party vendors handling ePHI, ensuring they also comply with HIPAA standards.
Adhering to these requirements helps in mitigating risks associated with data breaches and ensures the confidentiality, integrity, and availability of patient information.
Related Blog: Wearables vs. Professional Medical Monitoring Systems
How Data is Stored and Shared in RPM Systems?
RPM systems collect a vast array of patient data, including vital signs, medication adherence, and lifestyle information. The storage and sharing of this data involve complex processes that must prioritize security and privacy.
Data Storage Mechanisms:
Cloud-Based Solutions: Many RPM providers utilize cloud storage for scalability and accessibility. These platforms must be HIPAA-compliant, incorporating robust security measures like encryption and regular security audits.
On-Premises Servers: Some healthcare organizations opt for on-premises data storage to maintain direct control over data security.
Data Sharing Protocols:
Secure Transmission: Data is transmitted using secure channels, such as VPNs or encrypted APIs, to prevent interception during transfer.
Interoperability Standards: Adhering to standards like HL7 and FHIR ensures seamless and secure data exchange between different healthcare systems.
Patient Portals: Patients can access their data through secure portals, promoting engagement while maintaining privacy.
Implementing these mechanisms ensures that patient data remains secure throughout its lifecycle, from collection to storage and sharing.
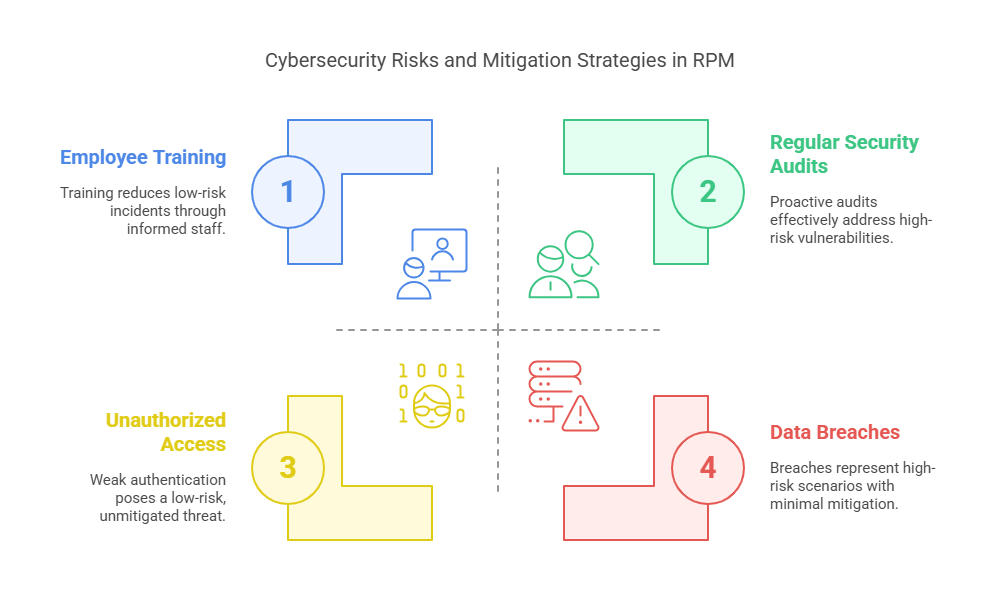
Cybersecurity Risks and Best Practices in RPM
The integration of technology in healthcare introduces various cybersecurity risks that can compromise patient data and safety. Understanding these risks and implementing best practices is essential for secure RPM deployment.
Common Cybersecurity Risks:
Unauthorized Access: Weak authentication mechanisms can allow unauthorized individuals to access sensitive data.
Data Breaches: Cyberattacks targeting healthcare systems can lead to significant data breaches, exposing patient information.
Device Vulnerabilities: RPM devices may have security flaws that can be exploited to manipulate data or device functionality.
Best Practices for Mitigation:
Regular Security Audits: Conducting periodic assessments helps in identifying and addressing vulnerabilities promptly.
Employee Training: Educating staff about cybersecurity practices reduces the risk of human error leading to security incidents.
Incident Response Plans: Establishing clear protocols for responding to security breaches ensures swift action to mitigate damage.
Firmware Updates: Keeping device firmware up-to-date addresses known vulnerabilities and enhances security.
By proactively addressing these risks, healthcare providers can protect patient data and maintain trust in RPM systems.
Related Blog: How Technology Is Changing the Way We Monitor Health
10 Lesser-Known Facts About RPM Data Security
FDA Warnings on Device Vulnerabilities: In early 2025, the FDA identified cybersecurity risks in certain patient monitors, highlighting the need for stringent device security. (Source)
SOC 2 Compliance Importance: Beyond HIPAA, SOC 2 compliance is crucial for RPM providers to ensure comprehensive data security and privacy. (Source)
Integration with EHRs: RPM data integration with Electronic Health Records (EHRs) enhances care coordination but requires robust security measures to protect data during exchange. (Source)
Use of AI in Data Analysis: Artificial Intelligence (AI) is increasingly used to analyze RPM data, necessitating secure algorithms to prevent data misuse.
Global Regulatory Variations: Data security regulations for RPM vary globally, requiring providers to adapt to different compliance standards.
Patient-Controlled Data Sharing: Some RPM systems empower patients to control who accesses their data, enhancing privacy and autonomy.
Blockchain for Data Security: Emerging use of blockchain technology in RPM offers immutable and secure data records.
Third-Party Vendor Risks: Vendors providing RPM services can pose security risks if not properly vetted and monitored.
Mobile Device Management (MDM): Implementing MDM solutions helps in securing RPM applications on mobile devices used by healthcare providers.
User Behavior Analytics: Monitoring user behavior can detect anomalies indicating potential security breaches in RPM systems.
Explore Courses for Clinical Research Career
Courses Available:
Conclusion
In conclusion, while remote patient monitoring offers immense benefits in modern healthcare, ensuring data security through HIPAA compliance, secure data handling, and robust cybersecurity practices is essential. As technology evolves in 2025, healthcare providers must remain vigilant, adopt industry best practices, and prioritize patient privacy at every step. With a commitment to data protection, organizations like CCRPS continue to lead the way in building safer, smarter healthcare systems.
Frequently Asked Questions (FAQs)
-
Yes, remote patient monitoring can be HIPAA compliant if it follows specific guidelines such as encrypting all transmitted and stored data, using access controls, maintaining audit logs, and ensuring that any third-party service providers sign Business Associate Agreements (BAAs). The key is implementing secure technology and workflows that align with HIPAA standards.
-
Patient data in RPM systems is typically stored in encrypted cloud-based servers or secure on-premise databases. HIPAA-compliant cloud providers use encryption both at rest and in transit. Access is restricted through role-based permissions and multifactor authentication, ensuring only authorized personnel can view or handle the data.
-
Some of the major threats include:
Unauthorized access through weak credentials
Exploits in device firmware or software vulnerabilities
Phishing attacks targeting healthcare staff
Man-in-the-middle attacks during data transmission
To combat these, best practices like regular software updates, encryption, employee cybersecurity training, and network monitoring are crucial.
-
Secure data sharing involves using encrypted channels (like VPNs or HTTPS), adopting interoperability standards such as HL7 and FHIR, and integrating RPM data directly into secure Electronic Health Record (EHR) systems. Providers must also verify that patient data access is logged and monitored regularly.